Immediate Response and Detection On Friday Microsoft released an official statement on its actions following a cyber breach by Nation State Actor Midnight Blizzard against its corporate systems. This breach raises concerns about the ongoing threat from nation-state actors and highlights potential shortcomings in Microsoft’s cyber practices. Common issues such as poor password management and… Read more »
Blog
The QR Code Quishing Threat: Unraveling the Risks
Despite having 2FA enabled, Mandiant, a Google-owned company, was recently the victim of a cyber-attack against their Twitter account with over 100,000 followers. To appear more legitimate, the hackers renamed the account “Phantom” and updated the bio to pose as the Phantom Cryptocurrency wallet. The hackers then used the account to promote links to a… Read more »
5 Essential Cybersecurity Measures for Healthcare Providers: A Guide to Protecting Patient Data

Healthcare organizations possess vast amounts of sensitive data that cybercriminals may find valuable, making them prime targets for cyberattacks. With the increasing volume of electronic patient data, it’s crucial to ensure the protection and confidentiality of this information. This post explores five essential cybersecurity measures that every healthcare provider should adopt to protect patient data…. Read more »
Google Settles Lawsuit for Tracking Users in Incognito Mode
Is your search activity truly private in private mode? Google has finally settled a lawsuit from June 2020 alleging that users were misled by having their activity tracked while browsing in incognito mode. According to The Hacker News, the plaintiffs filed a claim that Google violated federal wiretap laws by using Google Analytics to collect… Read more »
Can Hackers Still Bypass 2FA?
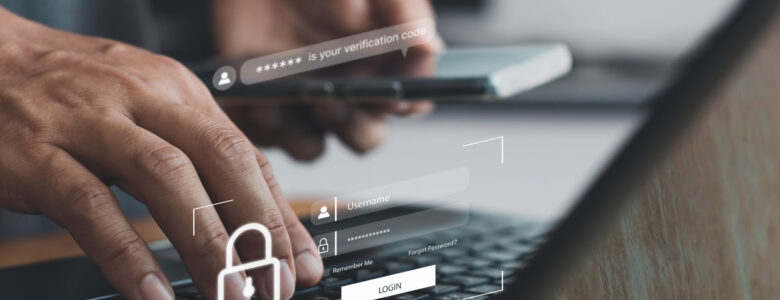
Despite having 2FA enabled, Mandiant, a Google-owned company, was recently the victim of a cyber-attack against their Twitter account with over 100,000 followers. To appear more legitimate, the hackers renamed the account “Phantom” and updated the bio to pose as the Phantom Cryptocurrency wallet. The hackers then used the account to promote links to a… Read more »
An Advanced iPhone Hack is Putting Apple Users at Risk
If you’re an Apple user, your data may be vulnerable to one of the most sophisticated attacks of 2023. A recent discovery by Russian cybersecurity company, Kaspersky, has brought to light an advanced spyware attack that was able to target Apple iOS devices. According to Hacker News, the attack, which was dubbed Operation Triangulation, used… Read more »
Is Your Smart TV Spying On You?
Are you planning to upgrade to a smart TV? You might want to think twice before making that purchase. According to a recent warning from an FBI field office, Smart TVs could leave owners vulnerable to advanced cyberattacks. Features of these high-tech devices include facial recognition, internet streaming, and microphone sensors – all of which… Read more »
Use of Blockchain Poses New Cybersecurity Risks
Blockchain technology is most commonly associated with cryptocurrencies, but it has many potential applications for cybersecurity. Blockchain is a decentralized ledger that records transactions securely and transparently. This makes it ideal for storing sensitive data such as financial records or personally identifiable information. However, the use of blockchain also poses new cybersecurity risks. For example,… Read more »
23andMe Data Breach Impacts 6 Million Users
23andMe, the popular genetic testing company, reported a data breach in October, which was later found to have impacted nearly 14,000 user accounts. Unfortunately, recent information has uncovered that the actual impact of the breach extended much further than a small fraction of users. According to Wired, the attackers collected the personal data of around… Read more »
Five Tips for Online Shopping Safely
The holiday season may be the busiest online shopping season of the year – but that also means it’s the busiest for eCommerce and phishing scams. According to Cybersource, phishing ranked as the leading form of eCommerce fraud in 2022, impacting 43% of global eCommerce merchants. Hackers deceive shoppers into revealing their personal or financial… Read more »





