Over the past year, cybercriminals have adopted artificial intelligence faster than most legitimate organizations. Tools that used to require technical expertise are now inexpensive, automated, and disturbingly convincing. For small organizations, this shift means one thing: traditional “see something suspicious” instincts are no longer enough.
Here is what leaders should expect — and how to prepare.
1. Deepfakes Will Move Beyond Celebrity Hoaxes
Deepfake tools can now clone voices, mimic faces, and generate realistic video instructions. Criminals are already using them to impersonate executives, request urgent payments, or authorize wire transfers.
What to do:
• Require multi-person approval for financial transactions.
• Train staff to verify unusual requests using a trusted secondary method (phone call, prior agreement, existing ticket).
• Document your escalation process so people are confident saying, “I need to confirm this first.”
2. Phishing Emails Will Look More “Human”
AI can write flawless messages, tailor them to your sector, and reference real events or staff names scraped from public websites. These emails are often polite, professional, and highly specific.
What to do:
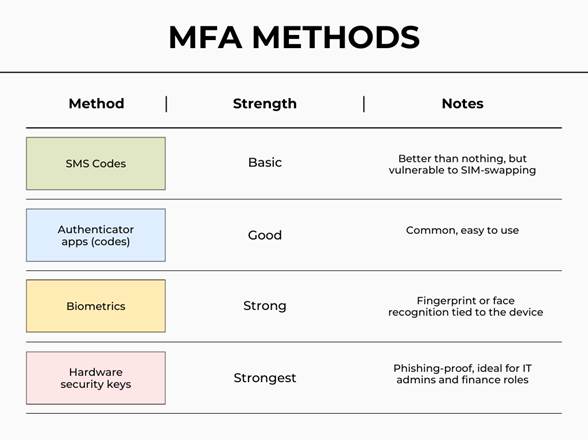
• Enable email filtering, link scanning, and MFA wherever possible.
• Teach people to hover over links, check sender domains, and slow down when urgency is used as pressure.
• Regularly simulate phishing to build awareness, not blame.
3. AI-Generated Support Scams Will Target Everyday Tools
Expect fake pop-ups, fraudulent “support” numbers, and spoofed login pages tied to platforms your team uses daily — Microsoft 365, QuickBooks, donation portals, scheduling tools, and more.
What to do:
• Create a simple rule: never call numbers or click prompts from error messages.
• Maintain a documented list of official support channels.
• Route suspected issues through IT, not directly to the “help” on the screen.
4. Data Will Be the Real Prize
AI scams are not only about stealing money. Credentials, donor/member data, healthcare information, and internal communications are far more valuable.
What to do:
• Limit who has access to sensitive systems.
• Turn on logging and review admin privileges regularly.
• Back up critical data, and make sure backups are tested.
The Bottom Line: Make Security Practical, Not Complicated
Small organizations do not need massive budgets to stay safe. What they need are clear expectations, consistent training, and basic controls that reduce human error.
If your team is unsure where to start, focus on three priorities:
- Multi-factor authentication on accounts that matter most.
- Documented processes for payments and approvals.
- Ongoing training that reflects real, modern attack scenarios.
AI has changed the threat landscape, but preparation, discipline, and the right safeguards still go a long way.
If you would like help reviewing your cybersecurity posture or training your team on emerging scams, we are happy to talk.