Previously, we have shown you how to delete and clear these pesky, residual elements in Internet Explorer that stick around on your computer after you’re finished searching the web. This time, we will be showing you how to do it for Microsoft Edge, their newest web browser. You’ll find updating to this browser comes with many benefits, it’s much faster than IE, and most elements are more user friendly, including spring cleaning of your data.
There are now two easy ways to clear all your data. The first is to click on the three lines in the upper right-hand corner which are the history icon.
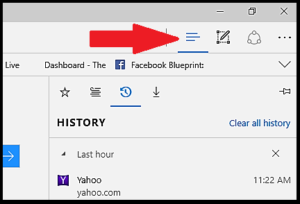
Once there, you can individually delete websites by clicking the “X” to the right of each site listed. Or you can delete all by clicking “Clear all history”. This will take you to the next screen where you can select up to eleven different data sets you wish you clear out, including your history, cache, cookies, and form data.
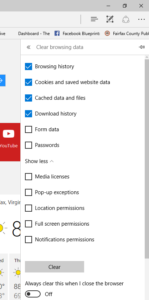
The other way you can access this same information is by clicking on the “more” icon in the upper right hand corner represented by three dots. From there you select “Settings”. On this page you can change your theme, make changes to how your tabs operate, and clear your browsing history, among other things. Once you click on “Choose what to clear”, it will take you to the same screen as shown above.
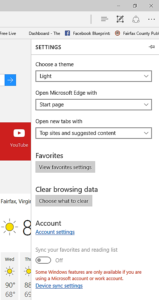
As you can see, this is far easier as you can delete all your data in one move, as opposed to having to delete your cache/cookies and history separately; not to mention any other data sets you wish to have stricken from the records. If you have any other questions, feel free to contact Optfinity anytime.





